Security Applications
Analytics to Detect and Mitigate Voice Threats and Attacks to Avoid Disruptions to Monetary and Data Loss
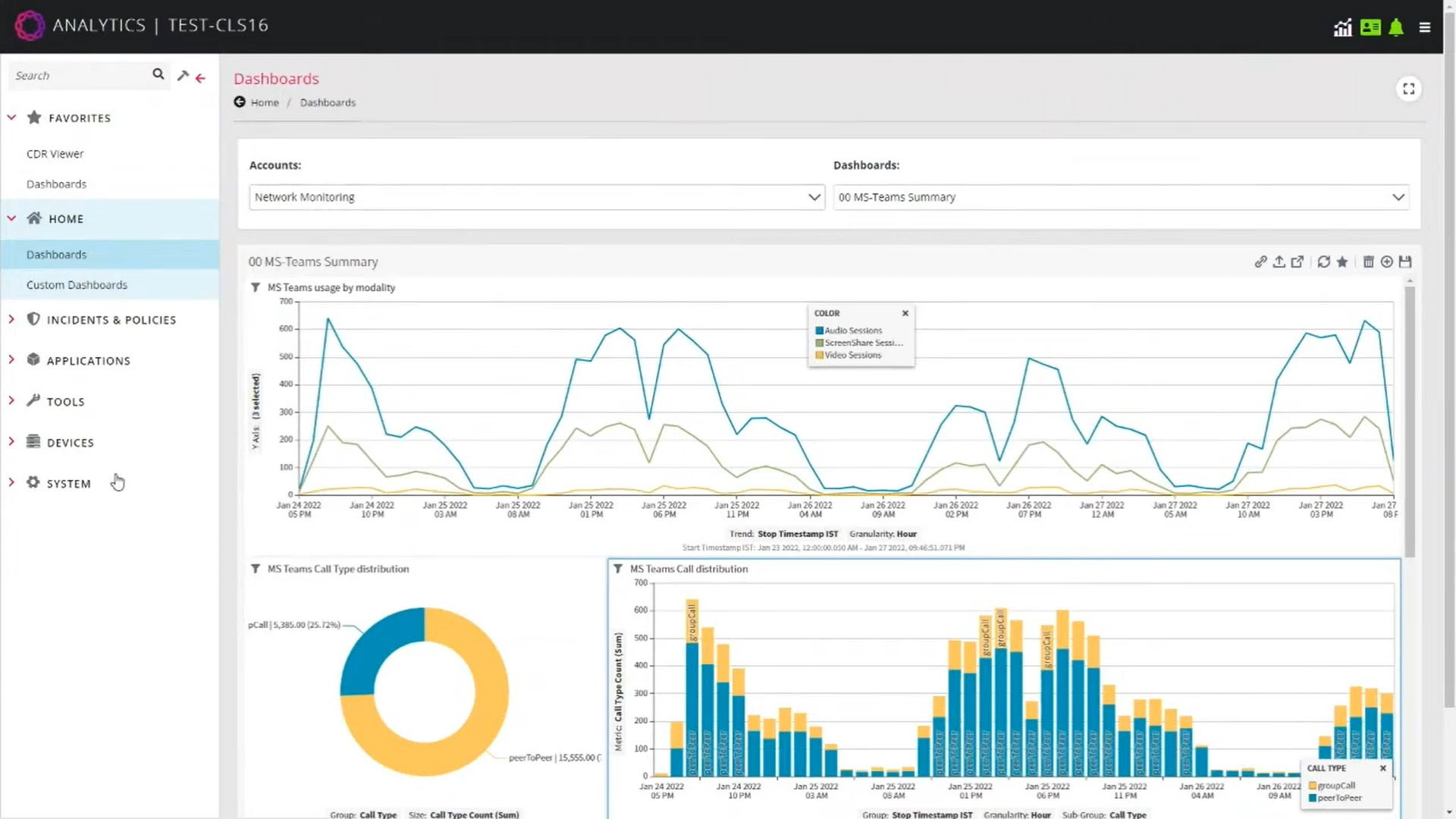
FraudProtect
Bad actors are attacking your unified communication or contact center networks to disrupt your business, to fraudulently use your resources or possibly even steal confidential data. Ribbon FraudProtect using machine learning models to recognize repetitive calling patterns that indicate potential voice threat and flag them in real-time based on destination detection. As more fraudulent calls are made they are quickly identified to prevent potential exposure that causes business disruption or loss. Once identified, this information is made available to Ribbon's Reputation Scoring service.
RoboProtect
Analysis using advanced databases, from national sources, to quickly identify the source of robocalls to enable policy decisions before they disrupt your employees or customers.
TDoSProtect
Unfortunately, even when you protect your unified communications from unwanted calls coming into your network it is still possible to encounter a malicious Telephony Denial of Service (TDoS) attack that ties-up communication applications such as IVRs or incoming and outgoing trunks. This security application uses advanced algorithm and machine learning techniques to identify these attacks. Advanced policies are applied at session border controllers to siphon out these unwanted, disruptive calls from your communications networks and applications.
NetProtect
The sharing of threat intelligence data (including white/blacklists) across network elements is the key to closing the security aperture of your communications network. This application enables the distribution of threat intelligence policies across network devices, so you can close the gap exposed by rogue communications. Distributed security policies between your SBCs and next-gen firewalls allows you to stop bad actors at the edge of the network. It also enables your organization to have a more effective and holistic security methodology across the converged (data and communication) network.

